Offensive Security Services
Keep Your Business Safe & Secure with Blue Bastion™
Blue Bastion’s Offensive Security Services team includes highly technical and experienced consultants whose goal is to make their own job more difficult. We do so by actively helping our clients and their security teams become better at identifying threat actor tactics, techniques, and procedures (TTPs). Both the offensive and defensive teams at Blue Bastion consistently work together to help each other’s skillset.
With access to our Security Operations Center’s toolset, including but not limited to Carbon Black and CrowdStrike, the Offensive Security team members test their skills and toolset against tools and techniques deployed by advanced blue teams.
Penetration Testing
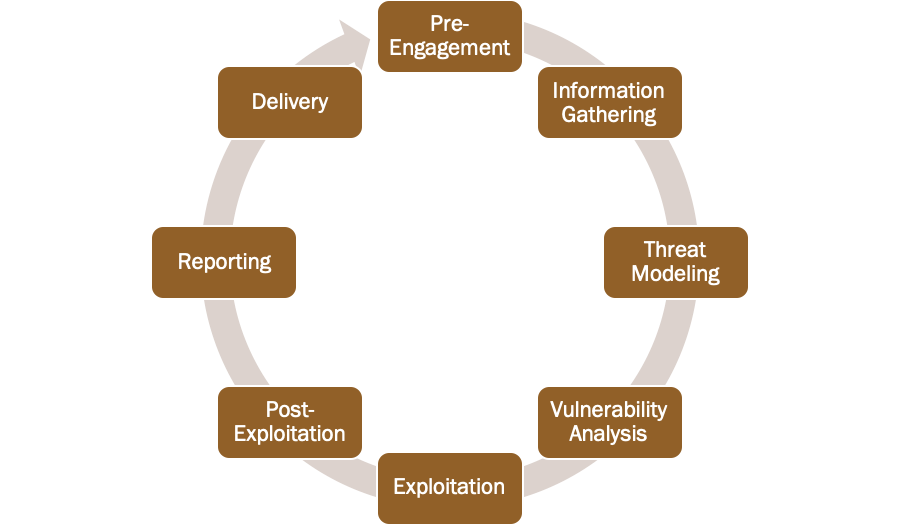
Blue Bastion conducts penetration testing based on Penetration Testing Execution Standard (PTES) guidelines. For an in-depth view of the PTES methodology, you can visit PTES Website.
The following is a high-level overview of Blue Bastion's penetration testing process and accepted methodology:
Application Penetration Testing
The web, API, or mobile application penetration testing aims to assess the in-scope service for vulnerabilities while following testing standards outlined by the Open Web Application Security Project. These include but are not limited to OWASP Top 10 (Web, API, and Mobile) and OWASP Web & Mobile Security Testing Guides. All web, mobile, and API penetration tests are performed as an authenticated user and an anonymous threat actor unless stated otherwise.
Blue Bastion’s penetration testers identify and exploit vulnerabilities using both automated and manual penetration testing Tactics, Techniques, and Procedures (TTPs) and report on the impact using evidence of validation and/or exploitation, as applicable.
External Penetration Testing
We’ll test your network from the perspective of an external attacker. We’ll identify whatever you have exposed to the internet, then demonstrate how an attacker might use them to compromise your organization.
Assumed Breach Internal Penetration Testing
We can simulate almost any scenario or threat actor, whether it’s a nation state, insider threat, or user compromised through a phishing email. We’ll work with you to identify weaknesses on your internal network, and provide specific, targeted recommendations for remediating everything we find.
Wireless Penetration Testing
We’ll work with you to identify and exploit weaknesses in how your wireless networks are configured to demonstrate how an attacker outside of your physical location might be able to breach your network.
Hardware Security Testing
Are you developing a new device? We’ll take it apart, poke it, prod it, and let you know what security flaws we find, along with proof of concepts to show them in action.
Cloud Security Assessments
Do you want to test your cloud presence? Regardless of where you’re hosted (Azure, AWS, GCP, etc.), we can work with you to identify weaknesses in your cloud infrastructure that an attacker might exploit to steal your data.
Physical Security Assessments
Whether adversarial or cooperative, we’ll test your physical infrastructure, to identify methods attackers could use to compromise your internal and external assets. The Blue Bastion team has years of experience performing physical assessments and ethical espionage throughout the public and private sectors.
Physical penetration testing focuses on testing the security of company facilities. These engagements can be done from many perspectives. On one end of the spectrum a tester might engage in social engineering during business hours looking to gain access to information or attach devices to a machine connected to the network. On the other end of the spectrum the tester or team of testers may replicate the threat of a burglar at 2:00 AM that will bypass alarms or perform other actions to achieve objectives. These engagements can replicate almost any attack path to gain access to a building targeting whichever assets are agreed upon.
Password Assessments
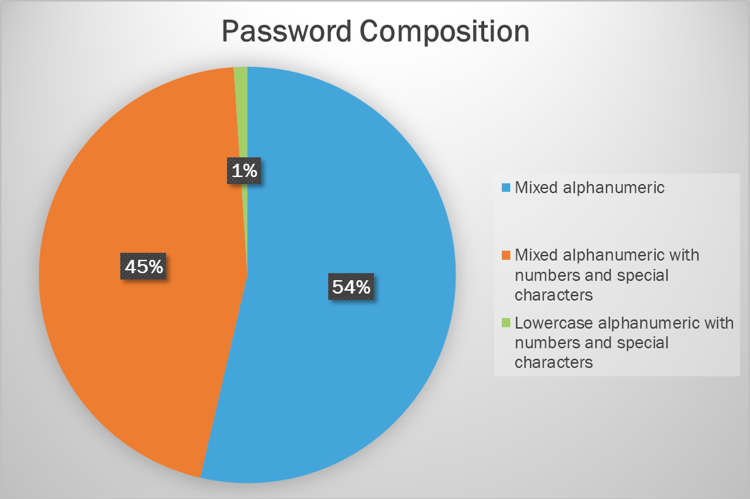
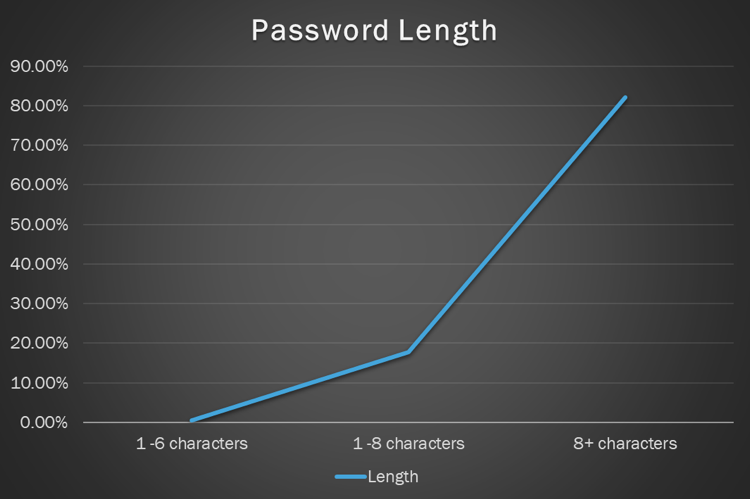
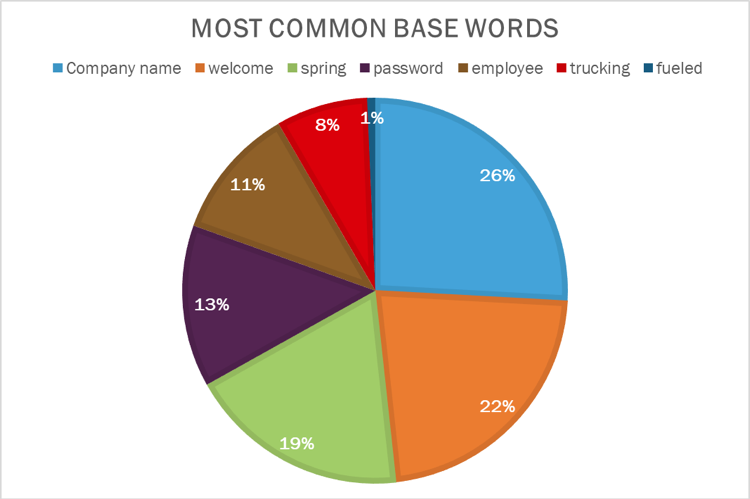
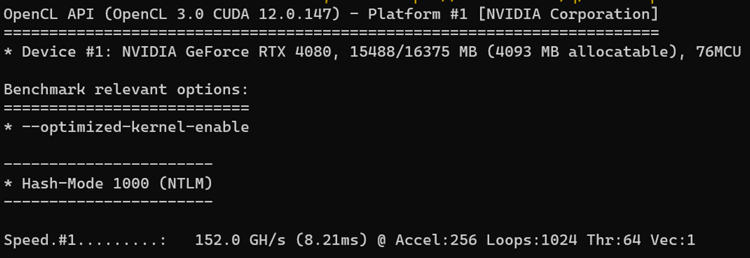
An eight-character alphanumeric password ending in a special character can be cracked quite easily with consumer-grade hardware. An NVIDIA RTX 4080 graphics card can crack a Windows password hash at 152.0 Giga hashes (GH) per second or 152 billion guesses per second.
Blue Bastion’s red team utilizes a combination of commonly used passwords, custom dictionaries based on the client’s environment, and brute force attacks to report on password hygiene.
Graphic examples of what this may look like include:
Red Team Adversary Emulation
Do you want to test your internal teams and security procedures? We can perform a stealthy red team assessment to test your people and processes. We can authentically replicate what an advanced attacker would do – without taking down your networks in the process.
Open-Source Intelligence (OSINT)
Do you want to find out what kind of information about your organization exists on the internet or dark web? We’ll do a deep dive into your organization’s external footprint and report back with what we find.
Identified information may include (but is not limited to):
Compromised credentials
Sensitive personal information
Protected company data
Blended Threat (Purple Teaming)
Using our team’s offensive and defensive skillsets, we’ll work collaboratively with your team to emulate attacks and validate your controls. We will then help develop improvements based on our assessment as an iterative process. We’ll show you how the attacks were accomplished and how such attacks may be detected. A reassessment will be carried out, to make sure improvements work as expected.
Social Engineering
Whether onsite, over the phone, or via email, Blue Bastion’s social engineers will use real-world scenarios tailored to your organization to assess the security awareness of your employees. Quit using easily identifiable templated phishing emails to train your team and start identifying weaknesses that are truly impactful to you.
Phishing
Phishing engagements are designed to test many different factors that affect company email security. These can include testing the efficacy of defensive systems (e.g., Proofpoint and Mimecast), identifying issues with employee response (missed warning signs), or altering perception of company environment safety. Blue Bastion can tailor a phishing engagement to meet any of these goals in various environments.
Pretext Calling
Pretext calling engagements target users, with the goal of obtaining information or persuading users to perform actions that may affect a company’s security posture. These engagements could be coupled with physical penetration testing, creating an expectation that a person will be coming to the business for a purpose; or with a phishing engagement, tricking the user into running malware or providing credentials.
Vulnerability Lifecycle Management
Blue Bastion’s blended threat emulation team utilizes open source and commercials tools to manage the lifecycle of your vulnerabilities and remediations.